Secure and monitor your enterprise's AI usage.
Secure every MCP request. Stop prompt injection, prevent data leaks, and stay in control with Perception's AI Gateway.
Built by professionals from forward-thinking companies.
Protect your organization from the risks of AI with our proxy
Direct and indirect prompt injections, PII or internal data leakage, identity, and so much more. AI introduces a new class of risks to your organization, and it's almost impossible to keep up with all of your other security priorities.
Not with Perception. Sign up, connect to Okta one click, and let us take care of your AI security stack. Our proxy automatically checks for PII or data leaks, prompt injections and blocks requests that violate your policies.
Please summarize the data on this user johndoe@gmail.com
Request rejected, PII detected
Oops!
Whitelisted models and MCP servers
43% of MCP servers contain command injection flaws, and your team still send requests to Deepseek. Don't risk it.
Use our whitelisted, secure MCP servers and model list with up-to-date risk assessments, or import your own servers and host them on our secure infrastructure so you can be sure queries are safe.
Internal Analytics MCP
Customer Data MCP
Experimental AI MCP
Perception Docs MCP
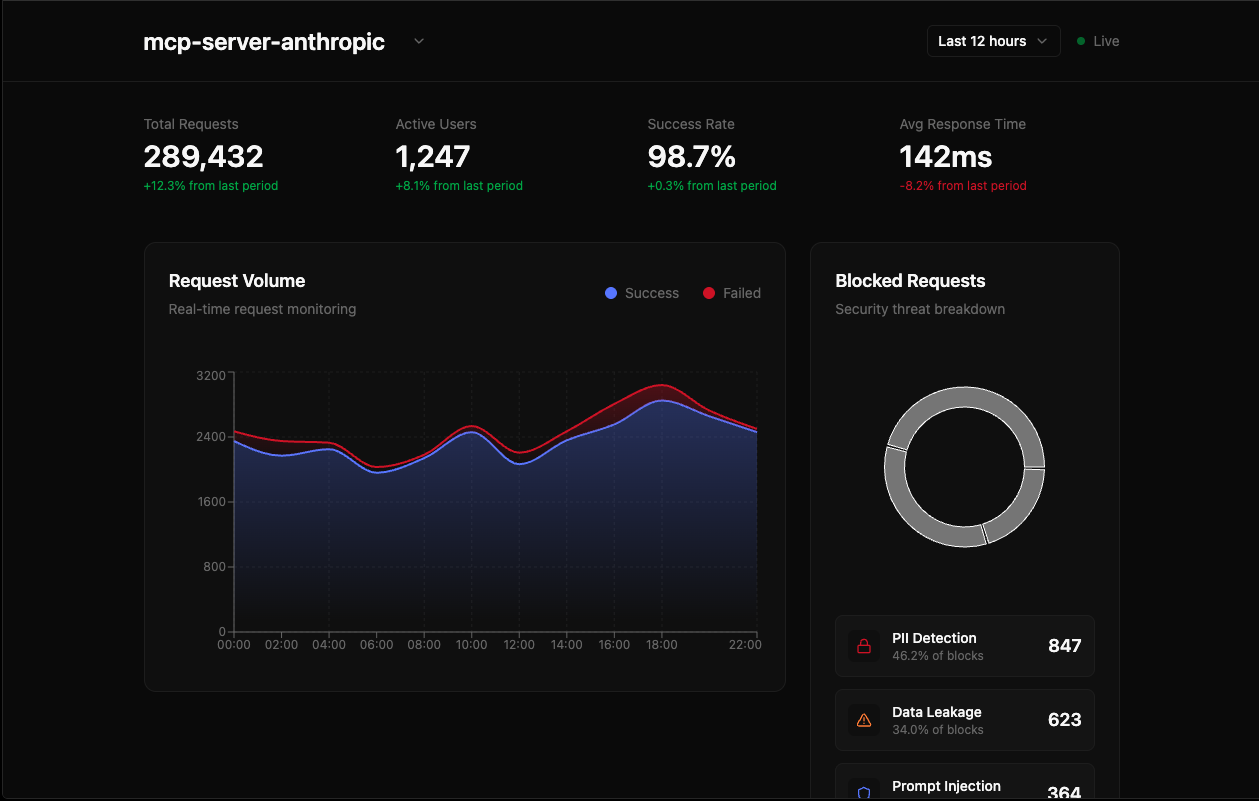
Observability and control over your internal AI usage
It's impossible to implement security rules when you don't even know how your team is using AI.
Perception fills the blank with built-in observability and dashboards to help you prioritize and understand usage.
View what models or MCP servers are being used, enforce custom policies or authorization controls, and roll them out one click.
Inference volume
Real-time request monitoring
Implement your AI security strategy today
No strings attached. We'll walk you through how we can help.